
Update: AMD has acknowledged the potential breach and has provided us with a statement.
RansomHouse, a relatively new data-extortion cybercrime group, has announced a major new victim. Today, the group published a new update on its darknet site and are claiming to have breached Advanced Micro Devices (AMD), the large chip manufacturing company.
RansomHouse is claiming to have breached AMD’s network and exfiltrated “more than 450 Gb” of data back in January 2022. The group has also published a data sample as evidence.
We examined the data sample that includes network files, system information, as well as AMD passwords obtained in the alleged breach. Below is the file tree of the sample that RansomHouse has published on its darknet website earlier today.
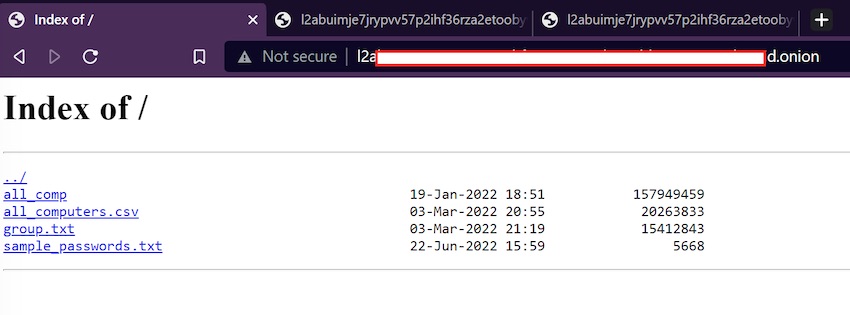
RestorePrivacy received a tip from RansomHouse that a sample of AMD data had already been leaked on the group’s website. We verified announcement and the information on the darknet.
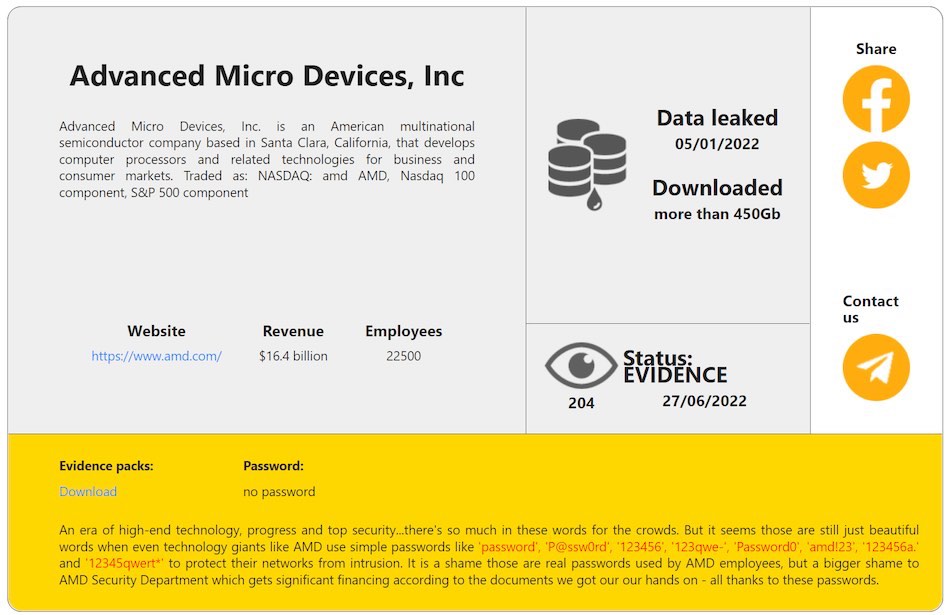
“Simple passwords” the cause of breach?
It’s no secret that hackers can easily launch attacks against networks with commonly-used passwords to to gain access.
According to RansomHouse, this was the case with AMD, which the group claims was using “simple passwords” to protect its network.
An era of high-end technology, progress and top security…there’s so much in these words for the crowds. But it seems those are still just beautiful words when even technology giants like AMD use simple passwords like ‘password’ … to protect their networks from intrusion. It is a shame those are real passwords used by AMD employees, but a bigger shame to AMD Security Department which gets significant financing according to the documents we got our our hands on – all thanks to these passwords.
– RansomHouse group
AMD is a multinational company based in Santa Clara, California. It is publicly traded on the NASDAQ stock exchange (AMD) with revenues of $16.4 billion for 2021.
While AMD is an long-established company, RansomHouse is relatively new. It burst onto the scene in December 2021 with a darknet website to publish the group’s exploits. RansomHouse also maintains a Telegram channel where it publishes updates.
Exactly one week ago on June 20th, the group announced via Telegram that it breached a major firm, and then held a contest to see if anyone could correctly guest the company. RansomHouse provided a riddle for people to guess the victim, as you can see below.
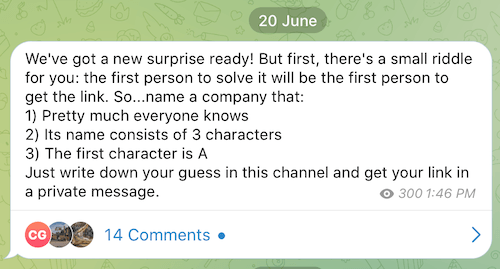
Source: RestorePrivacy.com
The answer finally appeared today with the group announcing that AMD was the victim.
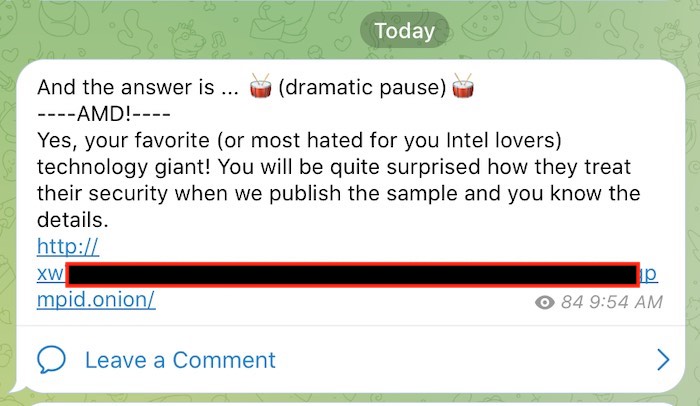
Source: RestorePrivacy.com
We will continue to analyze the sample and post any updates to this article as more information becomes available.
AMD provides RestorePrivacy with a statement
On June 27th, we reached out to AMD for comment. AMD provided us with the following statement on June 28th:
AMD is aware of a bad actor claiming to be in possession of stolen data from AMD. An investigation is currently underway.
-AMD Communications Director
RestorePrivacy is in contact with both AMD and RansomHouse and will update this article with any new information provided to us from either party.
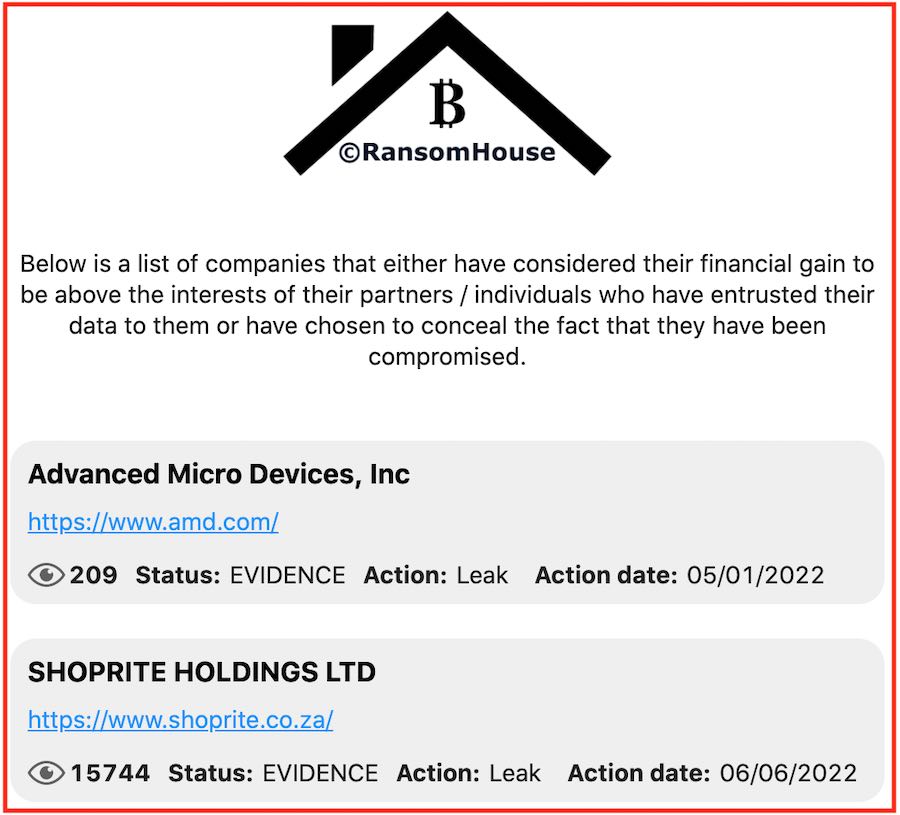
About RansomHouse group
RansomHouse first emerged in December 2021 with a darknet website that lists Saskatchewan Liquor and Gaming Authority (SLGA) as the first victim.
Earlier this month, RansomHouse gained international notoriety by leaking data that was breached from ShopRite, Africa’s largest retail chain.
With the addition of AMD today, RansomHouse’s darknet website lists a total of six victims from around the world. RansomHouse describes these victims as follows:
Below is a list of companies that either have considered their financial gain to be above the interests of their partners / individuals who have entrusted their data to them or have chosen to conceal the fact that they have been compromised.
-RansomHouse darket homepage
Here you can see a screenshot of the homepage with the last two victims:
A group of “professional mediators”
In contrast to other cybercrime organizations, RansomHouse does not actually claim to be a “ransomware” group.
They describe themselves as a “professional mediators community” on the group’s darknet About page.
Additionally, this group also claims to not actually produce ransomware or encrypt data, a noteworthy distinction from other notorious ransomware organizations. From the About section on the RansomHouse website:
We have nothing to do with any breaches and don’t produce or use any ransomware. Our primary goal is to minimize the damage that might be sustained by related parties. RansomHouse members prefer common sense, good conflict management and intelligent negotiations in an effort to achieve fulfillment of each party’s obligations instead of having non-constructive arguments. These are necessary and sufficient principles that lead to amicable agreements and sometimes even to subsequent productive and friendly cooperation.
Turning our attention back to AMD, we have not yet seen any notices or announcements about a data breach.
At the time this article was published, we have not yet received comment from AMD on the situation.
Updates:
June 28th: AMD has acknowledged the potential breach and provided RestorePrivacy with an official statement, added to the article above.

 Hacker Leaks Database Claiming to be from LendingTree
Hacker Leaks Database Claiming to be from LendingTree
Pluton Chip inside AMD APU. Game Over.
Once at work some glitch made my computer inaccessible. I called IT, they unglitched it and gave me a new password. I asked what it was and heard “password.”
Confused, I said “What’s my password again?”
“Password.”
“What?”
“It’s password, p-a-s-s-w-o-r-d.”
“Oh, I get it now.”
“You should probably change it. You have to every six months anyway.”
“OK, thanks.”
So, I didn’t change it for six months, then changed it to “password1,” followed by “password2,” and so on.
That’s one way stuff like this happens…
Hi Sven,
Great journalism!
Out of curiosity I searched around to see who else was reporting on the matter.
There were many major names in the online tech journalism industry who had;
And all but one referenced Restore Privacy as the source of the original investigation.
Great exposure for your site.
BoBeX
Hi Sven,
Thanks for the great article. I have a question for you:
How can I find/access the dark web websites of ransom groups? I want to access them for researching and educational purposes, not malicious. I am able to use Private Tabs with Tor in Brave.
Thanks!
Bad passwords strike again. Why don’t these corps force strong passwords? The solution seems so simple…
Maybe it’s not regular users, maybe it’s passwords for systems that they thought were behind enough security, like a printer server or something
Well. If they were inacessible enough – they wouldn’t need a password in the first place.
Or do you encrypt a database containing all your passwords with “password” because you think no one will ever get access to it? (good pw managers wouldn’t let you do that in the first place)